As so often, Blackbit is an early adaptor and, with Kubernetes, provides a new technology that stands for security, reliability in hosting and optimised processes in web development. Just at the right time, because the energy crisis and the war in Ukraine mean that the risk of cyber attacks is greater than ever before - for companies too.
Cyber security in times of crisis: increased threat situation
The energy crisis is becoming increasingly acute and the probability of a blackout following cyber attacks has risen even further in Germany since the start of the war in Ukraine. There have already been attacks on supply structures, fortunately without far-reaching consequences.
In its assessment of the current IT security situation in Germany, the Federal Office for Information Security (BSI) speaks of an "increased threat situation". It is not only government institutions and critical infrastructure that are at risk. Companies of all sizes are also targets of cyber attacks, primarily through ransomware, but also through elaborately prepared APT attacks.
Potentially threatening the existence of SMEs
2.6 million small and medium-sized enterprises (SMEs), which make up a whopping 99.4% of all German companies, are facing the challenge of digitalisation in Germany. At the same time, they are faced with the question of adequate cyber security. However, according to the BSI, the small and medium-sized enterprises among them are not in a position to ensure the operation and security of their information technology.
Phishing or ransomware attacks can have a life-threatening impact on these companies. The question for companies is therefore no longer just whether they will be the target of cyber attacks, but rather when. According to recent Statista surveys, the total damage caused by such attacks over the last twelve months totalled €202.7 billion.
The loss of revenue for individual companies increases with the duration of the downtime of service and shop sites as a result of a cyber attack. The loss of sensitive data, such as customer, shipping and payment data, as well as personal and company data, also weighs heavily.
Blackbit takes a secure approach with Kubernetes
With Kubernetes(K8s), Blackbit offers new technical answers to the current question of increased cyber security. K8s is an open source system for automating the deployment, scaling and management of containerised applications. Originally developed for internal purposes at Google, Google made the Kubernetes project available to a broad community as an open source platform in 2014. Kubernetes combines more than 15 years of experience in running production workloads with the best ideas and practices of the community. Kubernetes is therefore easy to expand and can be ideally customised to individual requirements.
Structural security: how Kubernetes works
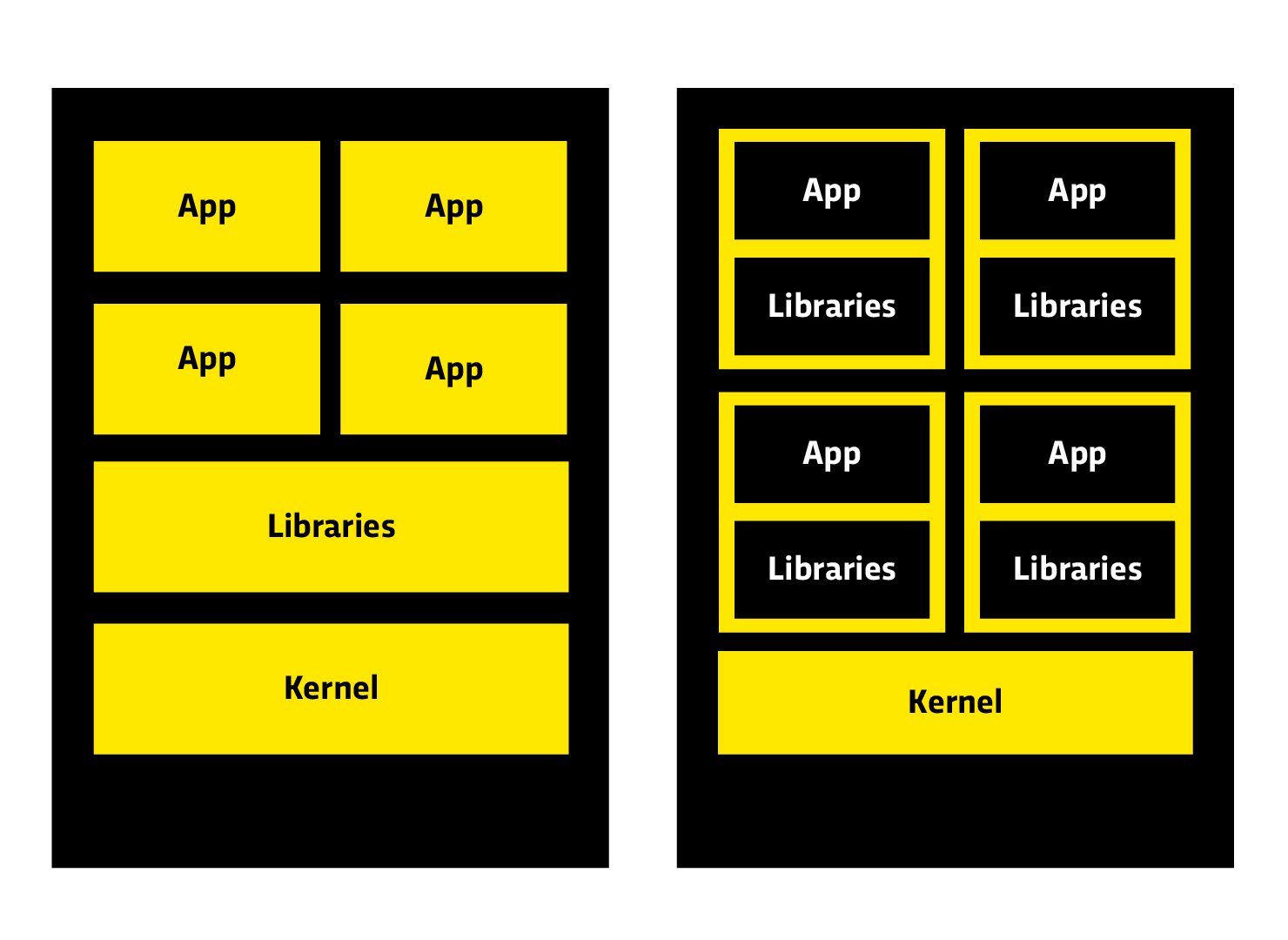 The classic structure without containers on the left and with containers on the right.
The classic structure without containers on the left and with containers on the right.
Divided into containers, an overall system is operated from basic resources that are located on several different servers or nodes. A single, rigid and therefore vulnerable system no longer exists in this revolutionary structure.
The individual containers contain no information about what the other containers are doing and can only execute the application for which they were created. It is therefore possible to execute a malicious script as part of a cyberattack, but the direct effects only affect the individual container and not an entire server.
In terms of security, Kubernetes therefore offers the following advantages:
- Ransom attacks are hardly possible
- Operating systems are automatically updated by deploying new containers. Old versions are not pulled along.
- As all containers are the same, this allows for simple security checks.
Kubernetes in hosting
The switch to the new hosting based on Kubernetes not only makes our service faster, more secure and more stable in use - the possible combinations of these technologies also offer you advantages: Benefit from the strengths of the technologies that we combine:
- Minimal coordination effort for maximum performance
Kubernetes controllers execute customised processes securely, reliably and automatically. - Continuous monitoring
Kubernetes constantly monitors the cluster and acts automatically to ensure stability and provide sufficient resources. - Flexibility through scaling
Whether running multiple applications or using additional servers - with Kubernetes there are numerous options for customised scaling, such as more performance or greater reliability. - A new level of security
Security updates can be installed much more easily as the automatically created containers are regularly tested by Blackbit for known vulnerabilities. As soon as a container is secure, it can be used by all applications.
Jan Fuchsmann, Lead DevOps Engineer at Blackbit and responsible for the Kubernetes project, summarises the biggest advantages of the new technology: "Kubernetes enables us to keep an eye on all systems and components at all times and thus react immediately and automatically to security events."
Smart combination of high-performance technologies
Blackbit combines powerful technologies to optimise the reliability and security of Kubernetes during operation. In conjunction with the Sysdig security software, Blackbit customers benefit from this additional service as an add-on, which, among other things, performs automatic vulnerability scans of running containers and can actively prevent unauthorised external access.
As a hosting solution for Pimcore X, Kubernetes takes your company's data management to a new level and protects the data you operate with every day - from customer data to payment and shipping information, which you are legally obliged to store and secure in compliance with GDPR.
Switch to Kubernetes now
Whether it's secure hosting or time-saving development and smooth deployment - all areas of application benefit from this structural security with Kubernetes.
Contactour sales team directly if you would like to find out more about the benefits of switching to Kubernetes for you and your company.
Do you have any questions or would you like a personal consultation?
The Best Digital Marketing Strategy for E-commerce
Extension for Asset Metadata Class Definition Bundle
Blackbit & Mailchimp at OMR 2025: Smart Tools, Powerful Campaigns
Blackbit at Pimcore Inspire 2025: Innovation, Expertise and New Solutions


Leave us feedback